Introduction
In an era dominated by digital advancements, the evolution of cybersecurity has become a pivotal narrative in the ongoing battle against cyber threats. As technology progresses, so do the tactics employed by cybercriminals. This article explores the historical development of cybersecurity, from its nascent stages to the cutting-edge solutions powered by artificial intelligence.
Prefer a video instead? Check it out below!
What is cybersecurity?
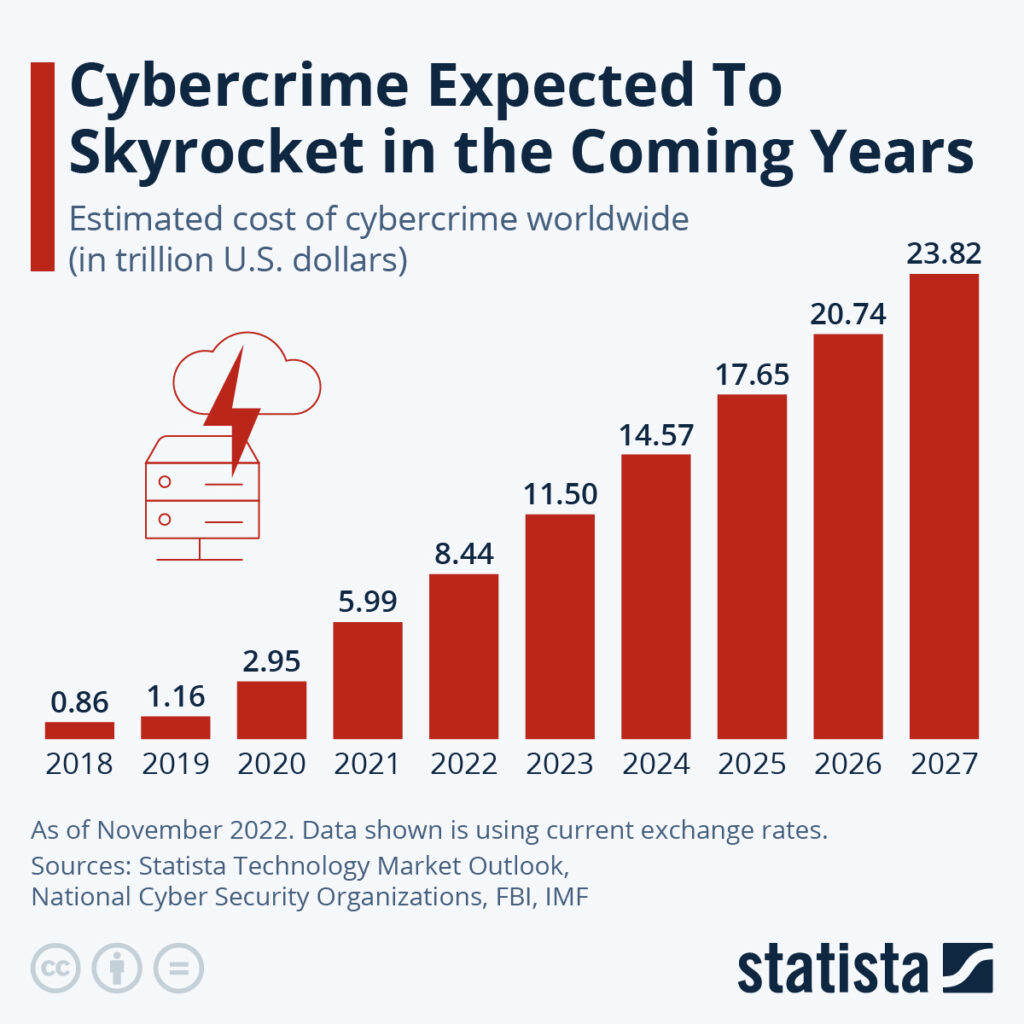
In its most basic sense, cybersecurity is the practice of protecting systems, networks, and programs from digital attacks and unauthorized access. Cyberattacks are becoming a problem of epic proportions. According to the National Cybersecurity Organization, the worldwide cost of cybercrime in 2023 stood at approx. 11.5 trillion USD, and that number is expected to rise to 23.8 trillion USD by 2027. Which is more than a 200% increase in as little as 3 years.
Early Cyber incidents (1900s)
Morris Worm: The Morris Worm, developed by Cornell University graduate student Robert Tappan Morris in 1988, was an early cyber threat that garnered significant media attention. Morris aimed to assess the size of ARPANET but inadvertently caused denial-of-service for 10% of connected machines. Exploiting Unix vulnerabilities, the worm spread through methods like exploiting service vulnerabilities, guessing passwords, and self-replication. What made this particular attack noteworthy was that it led to the first US felony conviction under the Computer Fraud and Abuse Act of 1986.
ILOVEYOU Virus: Fast forward a bit, and next we have the “ILOVEYOU” virus. The “ILOVEYOU” virus, also known as the Love Bug, surfaced in May 2000 as a destructive email worm. It was crafted by two Filipino computer programmers, both students at AMA Computer College, Philippines. Disguised as a love letter, it spread rapidly worldwide, infecting millions of computers by leveraging social engineering tactics. This incident highlighted the significance of cybersecurity measures and the risks associated with email attachments. It prompted a greater emphasis on educating users about safe computing practices and the importance of updated antivirus software to combat such threats.
Early Security Technologies
In response to these emerging threats, there was a need for security technologies. Two of the early protection options were antivirus software and firewall devices.

Antivirus Software
Antivirus software was an early defense tool for mitigating these security-related incidents. Having an up-to-date antivirus was a must. Some of the companies at the forefront of antivirus software are Kaspersky, McAfee, Norton, and Panda. This also began a huge marketing campaign when selling computers, as computer resellers would often advertise the computer as being bundled with reputable antivirus software.
Signature: These early solutions relied on signature-based detection, where specific patterns or signatures of known viruses were identified and targeted.
Heuristic Analysis: As the number of viruses increased, antivirus programs incorporated heuristic analysis, a method that allowed them to identify new, previously unknown viruses based on common behavioral patterns.
Firewalls
Another pretty popular security tool was hardware firewalls. These were devices that traditionally sat at the edge of your network and inspected traffic that transited from your internal network to the internet. Traffic was either allowed or denied based on the firewall policies; throughout the years, these firewall devices have gone through an evolution of their own.
1st Generation Firewalls: These firewalls functioned as packet filters, operating in a stateless manner to direct network traffic based on source and destination IP addresses and port numbers. For instance, TCP port 80 is standard for web servers, so firewall settings should permit traffic on this port for internal web servers. Conversely, blocking TCP port 3389 could prevent unauthorized remote desktop connections. While offering enhanced security, these firewalls had limitations; malicious content disguised within commonly used ports could evade detection as the firewalls couldn’t inspect network traffic directly.
2nd gen Stateful firewall: This is a network security tool that tracks the state of active connections. It monitors incoming and outgoing traffic and decides whether to allow or block packets based on the context of established connections. For example, it can permit incoming data packets if they’re part of an established outbound connection and deny those that aren’t. This helps enhance network security by filtering traffic more intelligently based on connection state.
Mid-2000s—Present day

Proliferation of cyber-attacks on enterprises
Fast forward to the mid-2000’s. In the 2000’s, we began to see a significant increase in the proliferation of cyberattacks on enterprises. Two breaches that stand out are the My Space and Yahoo breaches.
My Space (2013)
Though it had long stopped being the powerhouse that it once was, social media site MySpace hit the headlines in 2016 after 360 million user accounts were leaked onto both LeakedSource.com and put up for sale on dark web market The Real Deal with an asking price of 6 bitcoin (around $3,000 at the time).
According to the company, lost data included email addresses, passwords, and usernames for “a portion of accounts that were created prior to June 11, 2013, on the old Myspace platform. In order to protect users, My Space invalidated all user passwords for the affected accounts created prior to June 11, 2013, on the old Myspace platform. These users returning to Myspace will be prompted to authenticate their account and reset their password by following instructions.”
Yahoo Breach (2014)
This massive data breach occurred in 2014 and affected more than three billion Yahoo users. The hackers gained access to sensitive information such as names, dates of birth, addresses, and passwords. This breach had a major impact on the internet giant and its customers.
The Yahoo cyber-attack is the largest data breach in history. The sheer scale of the breach is staggering. Additionally, the sensitive information that was compromised could be used to commit identity theft and other crimes. The cyber-attack targeted 500 million accounts and obtained account names, email addresses, telephone numbers, date of births, hashed passwords, and some encrypted and unencrypted security questions.
The hackers were able to gain access to Yahoo’s system due to a single click on a spear phishing email, the FBI disclosed in 2016. Staff training regarding phishing is crucial currently and needs to be taken seriously by businesses of all sizes.
Legal and Regulatory Consequences: The breach resulted in legal consequences, with Yahoo facing lawsuits and regulatory scrutiny over its handling of the incident.
The incident also influenced the broader discussion on the legal responsibilities of companies in protecting user data.
Emergence of advanced persistent threats (APTs)

From 2010 until the present day, we’ve seen a drastic increase in APT attacks. APT (Advanced Persistent Threat) attacks are sophisticated and targeted cyber-attacks that are typically carried out by highly skilled and motivated adversaries, such as nation-states, organized crime groups, or corporate espionage units. APT attacks aim to breach a specific target network or organization and maintain unauthorized access over an extended period, often remaining undetected for a significant amount of time.
Here are some key characteristics of APT attacks:
• Sophistication: APT attacks often involve advanced techniques, such as zero-day exploits, custom malware, and social engineering tactics tailored to the target organization.
• Persistence: Unlike typical cyberattacks that aim for immediate gains, APT attackers are persistent and patient. They may spend months or even years infiltrating and navigating through the target network to achieve their objectives.
• Targeted: APT attacks are highly targeted towards specific organizations, industries, or even individuals. Attackers conduct thorough reconnaissance to gather intelligence about the target and tailor their attack strategies accordingly.
• Stealth: APT attackers prioritize remaining undetected within the target network for as long as possible. They employ stealthy techniques to evade detection by security defenses and monitoring systems.
• Objectives: The objectives of APT attacks vary widely and can include espionage, data theft, intellectual property theft, financial fraud, sabotage, or disruption of operations.
• Resourceful: APT attackers have significant resources at their disposal, including skilled personnel, advanced tools and technologies, and sometimes state-sponsored support.
Some recent examples of Advanced Persistent Threat (APT) attacks are:
SolarWinds (2019): The SolarWinds cyberattack was a significant supply chain attack attributed to APT29 (Cozy Bear), a Russian-state-sponsored APT group. The attackers compromised the SolarWinds Orion software platform, used by thousands of organizations for IT infrastructure management. This enabled the threat actors to infiltrate the networks of multiple high-profile targets, including U.S. government agencies and Fortune 500 companies.
Stuxnet (2010) : Discovered in 2010, Stuxnet was a highly sophisticated cyberattack orchestrated to sabotage Iran’s nuclear program by targeting SCADA systems responsible for uranium enrichment. Employing advanced techniques such as exploiting zero-day vulnerabilities, rootkit features, and encryption, Stuxnet suggested the involvement of a well-funded and technologically advanced entity, believed to be a state-sponsored collaboration involving the United States and Israel. The cyberattack successfully caused substantial damage to Iran’s centrifuges, illustrating the potential of cyber threats to inflict physical harm on critical infrastructure. Stuxnet left a legacy by significantly increasing global awareness of cybersecurity risks in critical sectors, emphasizing the need for international norms in cyberspace, and underscoring the importance of enhancing cybersecurity measures to protect against advanced and targeted attacks.
With the rise of APTs and sophisticated cyber threats, so too have defense mechanisms evolved. Organizations now use NGFW (Next Generation Firewalls), which offer far superior protection compared to their predecessors. NGFWs can make decisions based on what type of traffic is being transmitted, eg. ftp, web browsing, Netflix, etc. Another major advantage is that NGFWs examine the actual payload of the traffic for any malicious content, additionally it has features such as IDS, IPS, URL filtering and Antivirus.
Antivirus software has evolved to Endpoint Detection and Response (EDR). EDR solutions can detect threats across an environment, investigate the entire lifecycle of the threat, and provide insights into what happened, how it got in, where it has been, what it’s doing now, and what to do about it. EDR solutions can also help with rapid incident response, facilitating investigation, containment, and mitigation of security incidents. Other tools, such as Cyber Threat Intelligence play a pivotal role in the early detection and response of cyber incidents.
In addition to security tools, equally and sometimes more important was the introduction of security frameworks and compliance standards. In its most basic definition, a security framework/compliance standard is a group security controls that govern organizations.

A few popular ones are:
ISO/IEC 27001 (ISO/IEC 17799/BS 7799): The precursor to ISO/IEC 27001, BS 7799, was first published in the 1990s. ISO/IEC 27001, the international standard for information security management, was later introduced in the 2000s.
NIST Cybersecurity Framework (CSF): Developed by the National Institute of Standards and Technology (NIST), the CSF was introduced in 2014 as a response to growing cybersecurity threats. It provided a risk-based approach to managing and improving cybersecurity.
CIS Critical Security Controls: Originally known as SANS Critical Controls, this set of best practices was developed to address common cyber threats. The controls were formalized under the Center for Internet Security (CIS) in the early 2000s.
PCI DSS (Payment Card Industry Data Security Standard): Introduced in 2004, PCI DSS aimed to secure credit card transactions and protect cardholder data.
HIPAA stands for Health Insurance Portability and Accountability Act. It ensures that healthcare plans are accessible, portable, and renewable. It also sets standards for how medical data is shared across the U.S. health system to prevent fraud.
The domestic front has also seen the emergence of new cyber threats, one prominent one being that of IoT (Internet of Things). IoT refers to the network of interconnected devices embedded with sensors, software, and other technologies that enable them to collect and exchange data over the internet. These devices can include everyday objects like smart thermostats, wearable devices, industrial machinery, and more. For example, your echo dot, ring doorbell are considered iot devices.
Also, IoT adds a layer of convenience to our daily lives, there are also Potential Security Issues in IoT, which include:

Inadequate Authentication and Authorization:
Issue: Weak or default credentials can be exploited, allowing unauthorized access to IoT devices.
Resolution: Implement strong authentication mechanisms, use unique credentials, and regularly update passwords.
Privacy concerns: Issue: Potential access to your private home network if device is hacked.
Resolution: Employ network segmentation to isolate IoT devices from critical systems and data. This limits the impact of a potential compromise and reduces the attack surface. Utilize firewalls to control and monitor traffic between IoT devices and the broader network, allowing only authorized communication.
Insecure Firmware and Software:
Issue: Vulnerabilities in device firmware or software can be exploited by attackers.
Resolution: Regularly update and patch firmware and implement a secure software development lifecycle (SDLC).
Current and Future trends

What role does artificial intelligence play in the future development of cybersecurity?
According to digicert.com, by 2032, AI will have an estimated market size of $102 billion. So, we can safely say that AI is here to stay and will play a pivotal role in our daily lives as well as in business processes, cybersecurity being one of them. Its role spans various aspects, enhancing both offensive and defensive capabilities.
Potential threats of AI to data security
We are already seeing attackers use AI in attacks. For instance:
AI-automated malware campaigns: Cybercriminals can employ generative AI to craft sophisticated malware that adjusts its code or behavior to avoid detection. These “intelligent” malware strains are harder to predict and control, raising the risk of widespread system disruptions and massive data breaches.
Advanced phishing attacks: Generative AI has the capability to learn and mimic a user’s writing style and personal information, making phishing attacks considerably more persuasive. Tailored phishing emails, appearing to originate from trusted contacts or reputable institutions, can deceive individuals into divulging sensitive information, posing a substantial threat to personal and corporate cybersecurity.
Realistic deepfakes: Thanks to generative AI, malicious actors can now create deepfakes—highly convincing counterfeits of images, audio, and videos. Deepfakes pose a significant risk for disinformation campaigns, fraudulent activities, and impersonation. Picture a remarkably lifelike video of a CEO announcing bankruptcy or a fabricated audio recording of a world leader declaring war. These scenarios are no longer confined to the realm of science fiction and have the potential to cause significant disruption.
How AI can be used to strengthen cybersecurity?
On the bright side, AI can help transform cybersecurity with more effective, accurate, and quicker responses. Some of the ways AI can be applied to cybersecurity include:
Pattern recognition to reduce false positives: AI is great at pattern recognition, which means it can better detect anomalies, provide behavior analysis, and detect threats in real-time. In fact, a Ponemon Institute study in 2022 found that organizations using AI-driven intrusion detection systems experienced a 43% reduction in false positives, allowing security teams to focus on genuine threats. Additionally, AI-powered email security solutions were shown to reduce false positives by up to 70%.
Enable scale by enhancing human capabilities: AI can be used to enhance human capabilities, provide a faster response time, and offer scalability. The only limitation to scale will be the availability of data. Additionally, AI chatbots can be used as virtual assistants to offer security support and take some of the burden off human agents.
Speed up incident response and recovery: AI can automate actions and routine tasks based on previous training and multipoint data collection, offer faster response times, and reduced detection gaps. AI can also automate reporting, offering insights through natural language queries, simplifying security systems, and providing recommendations to enhance future cybersecurity strategies.
Sandbox phishing training: Generative AI can create realistic phishing scenarios for hands-on cybersecurity training, fostering a culture of vigilance among employees and preparing employees for real-world threats.
Effective Strategies for Strengthening Cybersecurity Defenses

As you probably realized by now, cybersecurity is a “big deal,” and it’s not going away anytime soon. However, the good news is that there are precautionary measures that we can take to help prevent and minimize cyberattacks. Below, I have included a few tips that both enterprises and individuals can take to help improve their security posture.
Enterprise
Conduct a Comprehensive Risk Assessment:
A crucial first step in building robust cybersecurity defenses is to conduct a thorough risk assessment. This involves identifying potential vulnerabilities, evaluating their impact, and understanding the likelihood of exploitation. By understanding the specific risks faced by your organization, you can prioritize your efforts and allocate resources effectively.
Implement Multi-Layered Defense Mechanisms:
Cybersecurity is not a one-size-fits-all solution. Implementing a multi-layered defense strategy is vital to protect against a wide range of threats. This includes deploying firewalls, intrusion detection systems, antivirus software, and implementing strong access controls. Additionally, consider adopting advanced technologies like behavioral analytics and artificial intelligence to detect and mitigate emerging threats.
Educate and Train Employees:
One of the weakest links in cybersecurity is human error. Employees must be educated about the importance of cybersecurity and trained in best practices for data protection. Regular awareness programs, phishing simulations, and training sessions can help create a security-conscious culture within the organization.
Stay Updated with Patches and Security Updates:
Cybercriminals exploit vulnerabilities in software and systems. Keeping all software and systems up to date with the latest patches and security updates is crucial. Establish a robust patch management process and monitor vendor notifications for any security vulnerabilities that may require immediate attention.
Leverage Encryption and Data Protection Measures:
Encrypting sensitive data both at rest and in transit provides an additional layer of protection. Implement strong encryption algorithms to secure confidential information, such as customer data or intellectual property. Additionally, consider implementing data loss prevention (DLP) solutions to prevent unauthorized data exfiltration.
Conduct Regular Security Audits and Penetration Testing:
Periodic security audits and penetration testing help identify vulnerabilities and validate the effectiveness of your cybersecurity measures. Engage external experts to conduct thorough assessments and provide recommendations for improvement. By regularly evaluating and testing your defenses, you can proactively identify and address any weaknesses before they are exploited.
Personal
Use Strong, Unique Passwords: Create strong passwords for online accounts and avoid using the same password across multiple accounts. Consider using a reputable password manager to generate and store complex passwords securely.
Enable Two-Factor Authentication (2FA): Enable two-factor authentication whenever possible. 2FA adds an extra layer of security by requiring a second form of verification, such as a code sent to your phone, in addition to your password.
Keep Software Updated: Regularly update operating systems, applications, and software programs on all devices. Software updates often contain patches for known vulnerabilities that hackers could exploit.
Keep Software Updated: Regularly update operating systems, applications, and software programs on all devices. Software updates often contain patches for known vulnerabilities that hackers could exploit.
Be Cautious of Suspicious Links and Attachments: Exercise caution when clicking on links or downloading attachments in emails, text messages, or social media posts, especially if they’re from unknown or untrusted sources. These could be phishing attempts or malware.
Use Secure Wi-Fi Connections: Avoid connecting to public Wi-Fi networks for sensitive activities like online banking or shopping. If you must use public Wi-Fi, consider using a virtual private network (VPN) to encrypt your internet connection.
Be Mindful of Personal Information: Limit the amount of personal information you share online, especially on social media platforms. Cybercriminals can use this information for identity theft or targeted attacks.
Backup Important Data Regularly: Regularly back up important files and data to an external hard drive, cloud storage service, or both. In the event of a cyberattack or data breach, having backups can help you recover your information without paying a ransom or suffering significant losses.
Use Antivirus and Antimalware Software: Install reputable antivirus and antimalware software on your devices and keep them up to date. These programs can help detect and remove malicious software from your system.
Educate Yourself About Cybersecurity Best Practices: Stay informed about common cyber threats and scams by reading cybersecurity blogs, news articles, and educational resources. Being aware of potential risks can help you recognize and avoid them.
Trust Your Instincts: If something seems too good to be true or feels suspicious, trust your instincts and proceed with caution. Don’t hesitate to verify the authenticity of emails, messages, or requests before acting.
In closing cybersecurity is mostly thought to be an “IT” thing but really and truly it’s an “everyone” thing. As a matter of fact, everyone has a part to play to ensure the safety of their digital identity and assets. If this article has been helpful to use, please let me know in the comment section, also consider subscribing to my Youtube Channel where I discuss all things Cybersecurity and Technology related.
Effective Strategies for Strengthening Cybersecurity Defenses
Enterprise Level


